Free CISA Certification Practice Questions:
 Alice wants to send a digitally signed message to
her friend Bob. All of the following statements
are true EXCEPT:
Alice wants to send a digitally signed message to
her friend Bob. All of the following statements
are true EXCEPT:A) Alice must apply a hash function to the message to create a message digest
B)Alice must encrypt the entire message with her private key
C) Bob must apply the same hash function as Alice to the message
D) Bob must decrypt the encrypted message digest using Alice's public key
E) If Bob is unable to verify the digital signature, either someone is trying to impersonate Alice or the message has been altered since Alice signed it
-
[Ans: B]
To create a digital signature for a message,
the data to be signed is encrypted by an
algorithm that takes as input the private
key of the sender. (Alice). Largely due
to performance reasons, the entire message
data is not typically encrypted, but rather
a digital thumbprint of the message (hash
/ digest) is created and then encrypted.
The hash of the message, which was encrypted
with the sender's (Alice) private key, acts
as a digital signature for that message.
The receiver (Bob) verifies the signature
by applying the same hash function as the
sender (Alice) to the message that was sent,
and decrypting the encrypted message digest
using the sender's (Alice) public key. If
the two values match, the receiver has successfully
authenticated the signature.
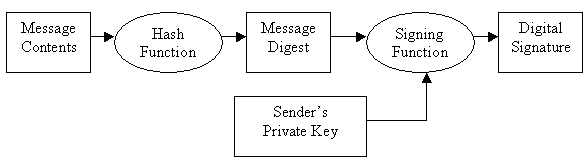
The digital signature is created as
follows:
1) The sender (Alice) of the message
uses a message digest function, such as
SHA-1, MD5 to create a message hash /
digest of the message contents.
2) The digest is then encrypted using
the private key of the sender.
3) This encrypted digest is then attached
to the message as the digital signature.
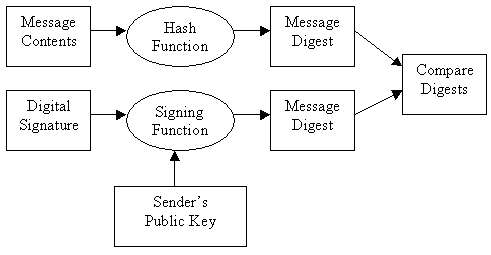
The digital signature is verified as follows:
1) The receiver of the message uses
the sender's public key to decrypt the
digital signature. If it decrypted successfully,
the receiver knows that the message came
from the holder of the private key.
If decryption of the digital signature
using the sender's public key fails,
someone may be attempting to impersonate
the sender.
2) The receiver then uses the message
digest function to calculate the hash
associated with the message contents.
If the hash is the same value as the one
decrypted from the digital signature,
the receiver can be confident that the
message was not altered or modified in
transit.
If the hash values are different,
the message may have been altered
after signing, or corrupted in transit.
In addition, if the sender and receiver
are using different hash functions
(MD5 versus SHA-1), the hash comparison
will also fail.
BACK | NEXT





